Managing Healthcare Cybersecurity Breaches – Part I
Healthcare faces constant cybersecurity threats, from ransomware attacks disrupting patient data access to phishing scams and insider threats. The sensitivity and high black-market value of healthcare records make the sector a prime target for cybercriminals.
This situation highlights the crucial need for comprehensive cybersecurity strategies, including risk assessments, staff training, incident response plans, and adherence to legal frameworks like the Health Insurance Portability and Accountability Act (HIPAA).
Given the inevitability of cybersecurity breaches, healthcare organizations must prioritize preparedness, moving beyond defensive measures to proactive prevention and strategic incident management.
Article Highlights
-
Healthcare organizations are prime targets for cyberattacks, due to the high value of patient data and complex digital infrastructures.
-
Common breach entry points include phishing emails, weak passwords, unpatched systems, and unsecured vendor access.
-
Preparation is the best defense, and organizations should have proactive cybersecurity policies, access controls, and employee training in place.
-
HIPAA compliance requires both prevention and response, making documentation and risk assessments essential.
-
A comprehensive breach response plan should include technical, legal, and communication strategies to reduce damage and restore trust.
What are Cybersecurity Breaches in Healthcare?
In healthcare, cybersecurity breaches are defined as an unauthorized access, use, disclosure, disruption, modification, or destruction of information. This encompasses electronic protected health information (e-PHI) that HIPAA aims to safeguard.
A breach compromises the confidentiality, integrity, or availability of patient information, potentially leading to identity theft, monetary loss, or harm to a patient’s privacy and trust.
The Department of Health and Human Services (HHS) clarifies that a breach entails “an impermissible use or disclosure under the Privacy Rule that compromises the security or privacy of the protected health information”.
Common Types of Cybersecurity Breaches
The healthcare industry encounters a myriad of cybersecurity breaches, each carrying the potential to disrupt services and exploit sensitive data. Here are some common types that healthcare organizations face:
- Ransomware: Ransomware attacks involve malicious software that encrypts files on a device or network, rendering them inaccessible to the rightful owners. Attackers then demand ransom for the decryption key. For healthcare facilities, this can mean locked access to critical patient records, hampering the ability to provide care.
- Phishing: Phishing scams are deceptive attempts to steal sensitive information such as usernames, passwords, and credit card details by disguising themselves as trustworthy entities in electronic communications. Healthcare staff might receive emails that appear to be from legitimate sources asking for sensitive information or urging them to click on malicious links.
- Insider Threats: Not all threats come from external actors; some originate from within an organization. Insider threats can include employees, contractors, or business associates who misuse their access to healthcare systems and data for malicious purposes or out of negligence.
- Advanced Persistent Threats (APTs): APTs are prolonged and targeted cyberattacks wherein attackers infiltrate a network to steal data over time. Healthcare organizations, with their wealth of patient data, are attractive targets for APTs aiming to exfiltrate e-PHI or intellectual property.
- Distributed Denial of Service (DDoS) Attacks: DDoS attacks aim to overwhelm healthcare IT systems with traffic, rendering them inoperable. This can disrupt healthcare operations, including access to electronic health records (EHRs) and communication systems.
- Data Breaches: Data breaches involve unauthorized access to or disclosure of personal health information. These breaches can occur through hacking, loss or theft of devices, unauthorized viewing of patient information, or accidental exposure due to software vulnerabilities.
Each of these threats underscores the critical need for comprehensive cybersecurity measures within healthcare organizations. The sensitivity of the data they hold not only mandates a robust security posture but also a proactive approach to identifying and mitigating potential cybersecurity risks.
As we navigate the complex landscape of healthcare cybersecurity, understanding these threats is the first step toward developing effective strategies to protect patient information and maintain trust in healthcare systems.

Pre-Breach Preparedness
The adage “prevention is better than cure” is particularly apt when it comes to cybersecurity in healthcare. Establishing a proactive stance through comprehensive pre-breach preparedness measures is essential for safeguarding sensitive health information against the increasing cyber threats.
This section outlines the foundational elements of pre-breach preparedness that healthcare organizations should implement.
Establishing a Healthcare Cybersecurity Framework
A cybersecurity framework provides a structured approach to managing and mitigating cybersecurity risks. For healthcare organizations, this involves adopting a framework that aligns with the unique regulatory, privacy, and patient care needs of the sector.
Frameworks such as the NIST Cybersecurity Framework or the HITRUST CSF offer guidelines that can be tailored to the specific operational and regulatory contexts of healthcare entities. These frameworks facilitate comprehensive risk management by categorizing best practices into core functions: Identify, Protect, Detect, Respond, and Recover.
Employee Training and Awareness Programs
Human error remains one of the leading causes of cybersecurity breaches in healthcare. Comprehensive employee training and awareness programs are vital to equip staff with the knowledge and skills needed to recognize and prevent cyber threats.
Training should cover topics such as recognizing phishing attempts, securing devices and passwords, and understanding the organization’s policies and procedures for handling sensitive information.
Regular, engaging training sessions, along with simulated phishing exercises, can significantly enhance employees’ ability to detect and respond to cybersecurity threats.
Implementation of Robust Cybersecurity Tools and Practices
Investing in advanced cybersecurity tools and adopting best practices is fundamental to protecting healthcare information systems. Key tools and practices include:
- Encryption: Encrypting data at rest and in transit ensures that even if data is intercepted or accessed by unauthorized individuals, it remains unreadable and secure.
- Multi-factor Authentication (MFA): MFA adds an extra layer of security by requiring users to provide two or more verification factors to gain access to IT systems, reducing the risk of unauthorized access.
- Access Controls: Implementing strict access controls ensures that only authorized personnel have access to sensitive information, based on their roles within the organization.
- Regular Software Updates and Patch Management: Keeping software and systems up to date with the latest patches is crucial for protecting against known vulnerabilities that could be exploited by cybercriminals.
- Incident Response Plan: Developing and regularly updating an incident response plan prepares organizations to respond effectively to cyber incidents, minimizing their impact.

Pre-breach preparedness is not a one-time effort but a continuous process that evolves with the changing cybersecurity landscape. By establishing a tailored cybersecurity framework, conducting regular risk assessments and audits, fostering a culture of cybersecurity awareness among employees, and implementing robust cybersecurity tools and practices, healthcare organizations can significantly enhance their resilience against cyber threats.
This proactive approach not only protects patient information but also preserves the trust and confidence of the patients who entrust healthcare providers with their most sensitive data.
Immediate Response to Cybersecurity Breaches
Initial Steps to Take Upon Discovering a Breach
- Identify and Document: The moment a breach is detected, it is crucial to document all known details about the incident, including the time of discovery, the nature of the breach (if known), and which systems or data are affected. This initial documentation will be vital for both remediation efforts and compliance with regulatory reporting requirements.
- Activate the Incident Response Plan: Every healthcare organization should have a comprehensive incident response plan that outlines specific procedures to follow in a breach. This plan should be activated immediately to guide the response efforts effectively.
- Notify Key Internal Stakeholders: Promptly inform key internal stakeholders, including the incident response team, senior management, and relevant department heads. Quick internal communication ensures that all parties are aware of the situation and can take appropriate actions as outlined in the incident response plan.
Assembling the Incident Response Team
An effective incident response team is a cross-functional group that includes members from IT/security, legal, compliance, communications, and senior management. Each member brings specific expertise critical to the breach response:
- IT/Security: Leads the technical investigation, containment, and remediation efforts.
- Legal: Advises on legal obligations and helps navigate potential legal ramifications.
- Compliance: Ensures the response is aligned with healthcare regulations, such as HIPAA, and other relevant privacy laws.
- Communications: Manages internal and external communication, including notifying affected individuals and coordinating with the media if necessary.
- Senior Management: Provides oversight and makes strategic decisions impacting the organization’s response and recovery.
Containing the Breach to Prevent Further Data Loss or System Compromise
- Isolate Affected Systems: Quickly isolating affected systems can prevent the spread of the breach to other parts of the network. This may involve disconnecting impacted devices from the internet or the internal network.
- Secure Physical Areas: If the breach involves physical theft or access, secure the affected areas to prevent further unauthorized entry or loss of sensitive information.
- Preserve Evidence: It is important to preserve evidence related to the breach for both the internal investigation and potential legal inquiries. This includes maintaining logs, system images, and access records.
- Eradicate the Threat: Once the immediate threat is contained, work on eradicating the source of the breach. This may involve removing malware, closing vulnerabilities, and enhancing security measures to prevent a recurrence.
- Recover Affected Systems: Begin the process of safely restoring affected systems and data from backups, ensuring that they are free from threats before reintegrating them into the operational environment.
Immediate response actions are the first phase in managing a cybersecurity breach. Swift coordinated efforts during this phase can significantly reduce the impact of the breach on the organization’s operations and reputation, while also fulfilling legal and regulatory obligations.
The steps outlined provide a roadmap for healthcare organizations to follow, ensuring a structured and effective response to cybersecurity incidents.
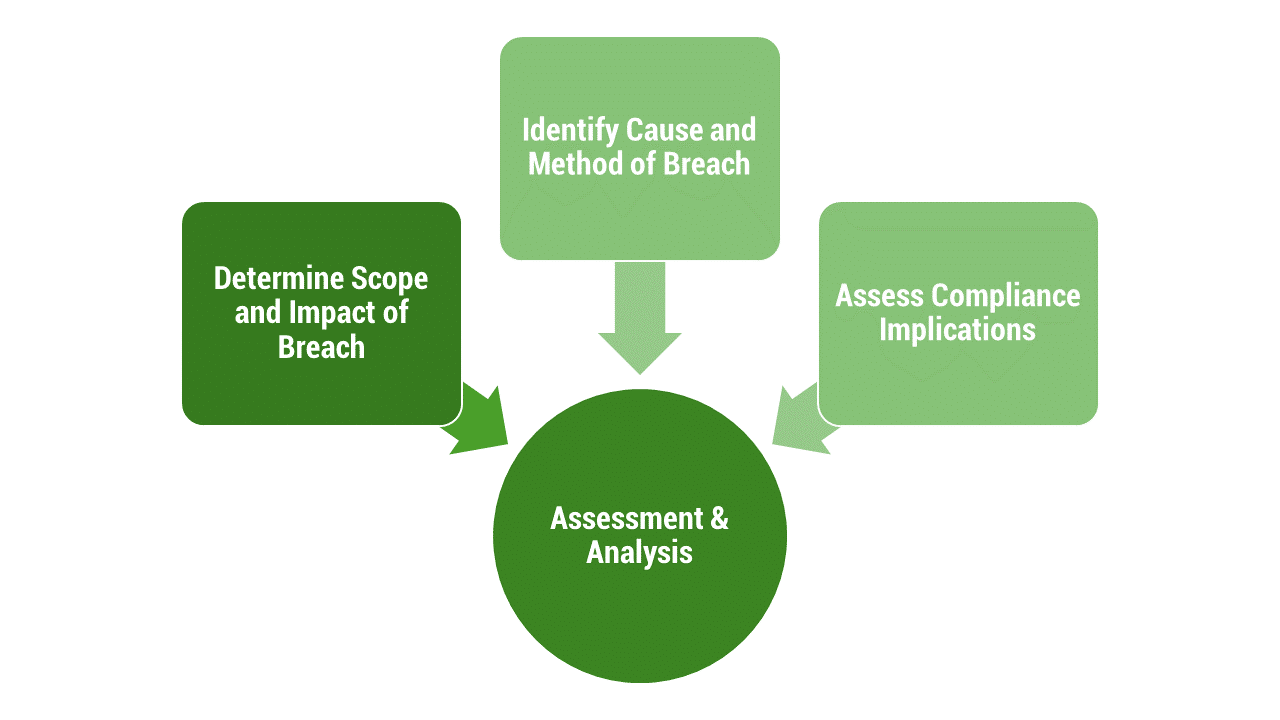
Assessment and Analysis
Determining the Scope and Impact of the Breach
- Data and Systems Assessment: Identify which data sets and systems were compromised during the breach. This includes determining the types of data accessed, whether they include sensitive patient information (e-PHI), and the volume of data affected. Understanding the data and systems involved helps in assessing the potential impact on patient privacy and organizational operations.
- Patient Impact Analysis: Evaluate how the breach might affect patients whose data was compromised. This involves considering the potential for financial fraud, identity theft, and the impact on patient trust and continuity of care.
- Operational Impact Assessment: Assess the breach’s impact on healthcare operations, including service disruptions, financial costs associated with the breach response, and potential revenue losses due to system downtimes.
Identifying the Cause and Method of the Breach
- Technical Forensics: Engage cybersecurity experts to conduct a forensic investigation into how the breach occurred. This might involve analyzing malware, examining system logs, and identifying exploited vulnerabilities.
- Breach Vector Identification: Determine the method used by attackers to gain unauthorized access. Common vectors include phishing emails, exploited vulnerabilities in software, or insider threats.
- Security Weaknesses: Identify any security weaknesses or lapses that allowed the breach to occur, such as outdated software, weak passwords, or lack of multi-factor authentication.
Assessing Compliance Implications, Particularly Concerning HIPAA
- HIPAA Breach Notification Rule Compliance: Determine the breach’s compliance implications under the HIPAA Breach Notification Rule, which mandates specific timelines and procedures for notifying affected individuals, the HHS, and, in some cases, the media.
- Risk Assessment Documentation: Conduct and document a risk assessment as required by HIPAA to evaluate the likelihood that the breached information has been compromised. The assessment should consider the nature and extent of the PHI involved, the unauthorized persons who used or disclosed the PHI, whether the PHI was acquired or viewed, and the extent to which the risk to the PHI has been mitigated.
- State and Federal Regulations: Beyond HIPAA, assess compliance with applicable state and federal privacy laws, which may have their own notification requirements and timelines that differ from HIPAA’s.
This phase of response is critical for healthcare organizations to understand the breach fully and take informed steps toward mitigation, recovery, and preventing future incidents. It lays the groundwork for developing a comprehensive action plan that addresses the immediate consequences of the breach and fortifies the organization’s cybersecurity posture against future threats.
By conducting a thorough assessment and analysis, healthcare organizations can navigate the complex regulatory landscape, fulfill their legal and ethical obligations to affected individuals, and restore trust in their ability to protect sensitive health information.

Notification and Disclosure
HIPAA Breach Notification Requirements
Under HIPAA, covered entities and their business associates must notify individuals affected by a breach of unsecured protected health information (PHI) without undue delay and no later than 60 days following the breach’s discovery. If the breach affects 500 or more individuals, the covered entity must also notify the Secretary of HHS and prominent media outlets serving the state or authority where the affected individuals reside.
The notification must include, to the extent possible:
- A description of what happened, including the date of the breach and the date of its discovery.
- The types of unsecured PHI that were involved (e.g., full name, Social Security number, date of birth).
- Steps individuals should take to protect themselves from potential harm resulting from the breach.
- A brief description of what the covered entity is doing to investigate the breach, mitigate harm to individuals, and protect against future breaches.
- Contact procedures for individuals to ask questions or learn additional information, which must include a toll-free number, an email address, a website, or postal address.
Communicating with Affected Parties: Patients, Employees, and Other Stakeholders
Effective communication following a breach is not just about regulatory compliance; it is about maintaining the trust of patients, employees, and other stakeholders. Organizations should strive for transparency in their communication while ensuring the protection of sensitive information during the notification process.
Communication strategies may include direct letters, emails (if the individual has agreed to receive electronic communications), and in cases where contact information is outdated or insufficient for 10 or more individuals, alternative methods such as posting notices on the organization’s website or press releases to media outlets.
Reporting the Breach to Relevant Authorities and Organizations
In addition to individual notifications, covered entities are mandated to report the breach to the HHS Office for Civil Rights (OCR) via their online portal. The timing and manner of these reports vary depending on the number of individuals affected:
- For breaches affecting 500 or more individuals, reports to the HHS OCR and local media must be made without unreasonable delay and no later than 60 days (about 2 months) from breach discovery.
- For breaches affecting fewer than 500 individuals, the covered entity may log the breaches and submit an annual report to the HHS OCR within 60 days of the calendar year’s end.
The notification and disclosure process are critical components of post-breach management, ensuring that affected individuals are informed and can take steps to protect themselves, and that regulatory obligations are fulfilled.
This process also serves to uphold the integrity and trustworthiness of healthcare organizations in the eyes of the public and regulatory bodies. Effectively managing this phase can significantly impact the organization’s recovery and the restoration of stakeholder confidence after a cybersecurity incident.
Conclusion
Check back for Part II of our two-part series where we dive into mitigation, remediation, legal considerations and potential liabilities, and post-breach recovery.
In the meantime, if you need assistance with a healthcare cybersecurity breach or need technical assistance, contact us today.
Ready to talk?





