HIPAA Security Standards are more critical today than many healthcare leaders realize. Cyber threats continue to grow in frequency and impact, while enforcement expectations are rising across the industry. What was once viewed as a compliance obligation is now a core operational risk that can disrupt care, expose patient data, and undermine organizational stability.
Yet we continue to see HIPAA security treated as a checkbox. Policies exist, assessments are completed, and training is documented, but the standards are not fully embedded into day-to-day decision-making. The result is a gap between technical compliance and real-world readiness.
Ultimately, HIPAA security outcomes are driven by leadership choices. Decisions about priorities, resources, and accountability shape whether security programs are resilient or fragile. This Insight examines why HIPAA Security Standards remain misunderstood and how leadership plays a defining role in turning compliance into meaningful protection.
Article Highlights
- HIPAA Security Standards require leadership attention, not just IT effort.
- Strong security practices reduce disruption, cost, and audit stress.
- Ongoing risk management works better than one-time compliance tasks.
- 1. Article Highlights
- 2. Understanding HIPAA Security Standards
- 3. Why HIPAA Security Standards Matter to Healthcare Leaders
- 4. Core Components of HIPAA Security Standards
- 5. Common Gaps in Meeting HIPAA Security Standards
- 6. HIPAA Security Standards in Different Care Settings
- 7. Building a Practical Approach to HIPAA Security Standards
- 8. Preparing for Audits and Enforcement
- 9. Conclusion
- 10. Ready to Talk?
- 11. Further Reading
- 12. Related Articles
Understanding HIPAA Security Standards
HIPAA Security Standards provide the foundation for how healthcare organizations protect electronic protected health information. While they are often discussed in technical or regulatory terms, their purpose is practical. They are designed to reduce risk, protect patients, and support reliable operations in an increasingly digital healthcare environment.
Rather than prescribing a single way to achieve compliance, HIPAA Security Standards establish a framework for identifying risk and applying safeguards that make sense for an organization’s size, complexity, and operating environment. When understood clearly, they help leadership teams move from reactive compliance to intentional, defensible decision-making.
What HIPAA Security Standards Are Designed to Do
HIPAA Security Standards exist to protect electronic protected health information wherever it is created, stored, accessed, or transmitted. This includes clinical systems, billing platforms, reporting tools, mobile devices, and third-party environments that support care delivery and operations.
The standards are built around three core objectives:
- Protecting confidentiality so information is only accessible to authorized individuals
- Preserving integrity so data is not altered or destroyed improperly
- Ensuring availability so information is accessible when needed to support care and business functions
A defining feature of HIPAA Security Standards is flexibility. The standards recognize that healthcare organizations differ significantly in scale, resources, and risk exposure. What is reasonable for a small ambulatory clinic will not look the same as what is required for a multi-site health system. This flexibility allows organizations to tailor safeguards, but it also places responsibility on leadership to understand risk and document decisions thoughtfully.
Flexibility does not lower the bar for compliance. It raises expectations for judgment, accountability, and ongoing oversight.
How HIPAA Security Standards Differ from Privacy Standards
HIPAA Privacy Standards focus on how protected health information may be used and disclosed. They establish patient rights and define appropriate handling of information across the organization.
HIPAA Security Standards address a different question. They focus on how electronic information is protected in practice. This includes administrative processes, technical controls, and operational safeguards that prevent unauthorized access, loss, or disruption.
Privacy policies alone cannot protect information without security controls to enforce them. Most security failures are not intentional violations. They stem from weak access management, poor system configuration, limited monitoring, or unclear responsibility. This is why security must be treated as an operational discipline, not just a compliance requirement.
For organizations that want help translating requirements into practical, defensible actions, our HIPAA compliance and security advisory services support leaders in aligning governance, operations, and IT safeguards with real-world risk.
Why HIPAA Security Standards Matter to Healthcare Leaders
HIPAA Security Standards are often discussed as a technical or compliance concern, but their impact is far broader. For healthcare leaders, these standards represent an enterprise risk issue that touches governance, operations, finances, and trust. How leadership approaches HIPAA security directly influences an organization’s ability to withstand disruption and respond effectively when incidents occur.
When security is viewed as an IT responsibility alone, organizations tend to focus on tools and tactics. When it is viewed as a leadership responsibility, organizations focus on risk, accountability, and long-term resilience. That shift in perspective is what separates minimal compliance from meaningful protection.
HIPAA Security Standards as a Governance Issue
HIPAA Security Standards require active oversight from boards and executive teams. While technical teams may implement controls, leadership is responsible for setting expectations, approving risk tolerance, and ensuring that security decisions align with organizational priorities.
Key governance responsibilities include:
- Ensuring regular and meaningful security risk discussions at the executive and board level
- Understanding where risk is being accepted versus mitigated
- Confirming that security roles, responsibilities, and escalation paths are clearly defined
Risk acceptance is a leadership decision, not a technical one. Choosing to delay an investment, rely on a workaround, or accept known gaps has consequences that extend beyond compliance. These decisions should be deliberate, documented, and revisited as the threat landscape and operating environment change.
Organizations with strong governance treat HIPAA security as part of enterprise risk management. They ask not only whether controls exist, but whether they are adequate for the level of risk the organization is carrying.
The Operational and Financial Impact of Security Failures
Security failures rarely stay contained within IT systems. They disrupt care delivery, divert leadership attention, and strain already limited resources. Downtime can delay appointments, interrupt clinical workflows, and force staff into manual processes that increase the risk of error.
The financial impact can be just as significant. Incident response costs, system recovery, legal expenses, and potential penalties add up quickly. Long after systems are restored, organizations often continue to feel the effects through increased insurance premiums, unplanned technology spending, and lost productivity.
Perhaps most damaging is the loss of trust. Patients, partners, and communities expect healthcare organizations to protect sensitive information. When that trust is compromised, rebuilding confidence can take years and requires sustained leadership effort.
For healthcare leaders, HIPAA Security Standards are not about avoiding a single bad outcome. They are about protecting the organization’s ability to deliver care, maintain credibility, and operate with stability in an increasingly complex risk environment.

Core Components of HIPAA Security Standards
HIPAA Security Standards are often perceived as complex because they span multiple areas of an organization. In reality, the requirements fall into three clear categories. Administrative, physical, and technical safeguards work together to protect electronic protected health information and reduce risk across people, processes, and systems.
Understanding these categories helps leaders see where responsibilities sit and how gaps in one area can undermine controls in another.
Administrative Safeguards
Administrative safeguards form the foundation of a strong HIPAA security program. They focus on how organizations identify risk, establish expectations, and prepare their workforce to protect information.
At the center of these safeguards is risk analysis and risk management. Organizations are expected to regularly assess where electronic protected health information is vulnerable and take reasonable steps to reduce those risks. This is not a one-time exercise. As systems, vendors, and workflows change, risk must be reassessed and addressed.
Policies, procedures, and workforce training translate risk decisions into daily behavior. Clear policies define how systems should be used and protected. Training ensures staff understand their role in safeguarding information and responding to potential incidents. Without consistent reinforcement, even well-written policies lose effectiveness.
Administrative safeguards are where leadership intent becomes operational reality.
Physical Safeguards
Physical safeguards address how facilities and devices are protected from unauthorized access. While they may seem straightforward, they are often overlooked as environments evolve.
Facility access controls limit who can enter areas where systems and sensitive information are located. This includes offices, data centers, and clinical spaces where workstations are used. As organizations expand, relocate, or adopt hybrid work models, physical access controls must adapt.
Device and workstation security focuses on how computers, laptops, tablets, and other devices are used and protected. Lost devices, shared workstations, and unsecured equipment remain common sources of risk. Clear expectations and practical controls help reduce exposure without disrupting care delivery.
Physical safeguards reinforce that security extends beyond software and networks.
Technical Safeguards
Technical safeguards protect electronic protected health information within systems and during transmission. These controls are often the most visible, but they are only effective when aligned with administrative and physical safeguards.
Access controls ensure users can only access the information they need to perform their roles. This includes unique user identification, role-based access, and timely removal of access when roles change.
Audit controls allow organizations to monitor system activity and identify unusual or inappropriate behavior. Without visibility into system use, potential issues can go undetected for long periods.
Transmission security protects information as it moves between systems, devices, and external partners. Encryption and secure communication methods help prevent interception and unauthorized access during data exchange.
Together, these technical safeguards help enforce policy decisions and support accountability across the organization.
Common Gaps in Meeting HIPAA Security Standards
Most organizations do not struggle with HIPAA Security Standards because they ignore them. They struggle because implementation breaks down in predictable ways. On paper, programs often look complete. In practice, controls are inconsistently applied, poorly governed, or disconnected from daily operations.
These gaps tend to emerge not from a lack of effort, but from competing priorities, limited resources, and unclear ownership.
Risk Assessments That Exist on Paper Only
Risk assessments are a foundational requirement, yet they are one of the most common weak points. Many organizations complete an assessment once, often to satisfy an audit or external request, and then move on.
Common issues include:
- One-time assessments that are not revisited as systems, vendors, or workflows change
- Identified risks that are documented but never formally addressed
- Lack of ownership for tracking remediation and timelines
Without follow-through, risk assessments become static documents rather than tools for decision-making. When incidents occur, these gaps are often exposed quickly, especially if leadership cannot demonstrate how known risks were evaluated and managed over time.
Overreliance on Technology Without Process
Technology plays an important role in protecting information, but tools alone do not create compliance. Organizations often invest in security software expecting it to solve underlying problems without the supporting processes needed to make it effective.
We frequently see:
- Security tools implemented without clear governance or accountability
- Alerts generated but not consistently reviewed or acted upon
- Assumptions that vendors or managed service providers are responsible for compliance
Vendors can support security, but responsibility always remains with the organization. Without defined processes, escalation paths, and oversight, even sophisticated tools provide limited protection.
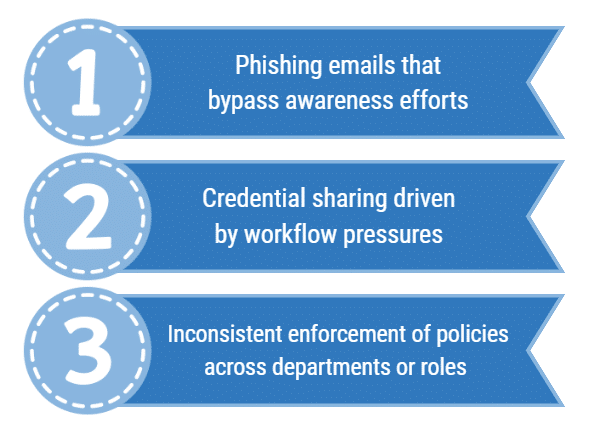
Workforce Behavior and Training Challenges
The workforce remains one of the most significant sources of risk. Even strong technical controls can be undermined by inconsistent behavior or unclear expectations.
Common challenges include:
Training is often delivered annually and then forgotten. Effective programs reinforce expectations throughout the year and align policies with how staff actually work. When enforcement varies or exceptions become routine, risk increases quietly until an incident brings it to the surface.
Addressing these gaps requires more than additional controls. It requires leadership attention, realistic processes, and a willingness to align security expectations with operational reality.
HIPAA Security Standards in Different Care Settings
While HIPAA Security Standards apply across healthcare, the way risk shows up varies significantly by care setting. Organizational structure, patient populations, technology use, and available resources all influence how security challenges emerge and how they should be addressed. Leaders are most successful when they recognize these differences and tailor their approach rather than relying on a one-size-fits-all model.
Tribal Health Organizations
Tribal health organizations often operate within unique constraints that directly affect HIPAA security efforts. Limited funding, workforce shortages, and aging infrastructure can make it difficult to implement and sustain security controls at the same pace as larger systems.
At the same time, sovereignty considerations and shared services add layers of complexity. Tribal organizations may rely on shared EHR platforms, regional IT services, or external partners, which can blur lines of responsibility if governance is not clearly defined. Leadership must balance regulatory expectations with cultural values, community trust, and practical realities.
Strong programs focus on clear risk ownership, realistic prioritization, and documented decision-making. Our tribal health consulting services support leaders in aligning HIPAA security efforts with sovereignty considerations and operational capacity.
Behavioral Health Providers
Behavioral health providers face heightened risk due to the sensitivity of the data they manage. Information related to mental health, substance use, and treatment history carries significant privacy implications and can cause real harm if improperly disclosed.
Remote access and telehealth have expanded access to care, but they have also increased exposure. Clinicians' accessing systems from multiple locations, use of personal devices, and reliance on virtual platforms introduce new vulnerabilities if safeguards are not well defined and enforced.
Leadership teams in behavioral health organizations must pay close attention to access controls, monitoring, and workforce practices. Our behavioral health consulting services help organizations address these risks while supporting flexible, patient-centered care models.
Ambulatory Care and Outpatient Clinics
Ambulatory care and outpatient clinics often experience rapid growth, whether through expansion, mergers, or increased service lines. Growth can outpace governance, leaving security controls inconsistent across locations and systems.
Third-party vendors and system integrations are another major source of risk. Scheduling platforms, billing services, patient engagement tools, and specialty systems all introduce access points to electronic protected health information. Without strong vendor oversight and integration management, gaps can form quickly.
Leaders in ambulatory settings benefit from scalable security frameworks that grow with the organization. Our ambulatory care consulting services support clinics in strengthening governance, vendor management, and security practices as operations expand.

Building a Practical Approach to HIPAA Security Standards
A practical approach to HIPAA Security Standards goes beyond checking boxes. It requires leadership focus, clear priorities, and steady follow-through. The goal is not perfection. The goal is to reduce real risk in ways the organization can sustain.
Strong programs are built to work in the real world. They support staff. They fit operations. They hold up when something goes wrong.
Starting with an Honest Risk Analysis
Every effective security program starts with an honest risk analysis. This means clearly defining scope. Systems, vendors, devices, and workflows all need to be included.
Problems arise when assessments are too narrow. Gaps also appear when leadership is not aligned. Leaders must understand what risks exist and which ones are being accepted.
Risk tolerance is a leadership decision. It should be discussed openly and documented clearly. When leaders are aligned, risk analysis becomes a decision-making tool, not just a report.
Aligning Policies, Technology, and Daily Operations
Security only works when policies, technology, and daily operations support each other. Policies should reflect how people actually work. Technology should make secure behavior easier, not harder.
If controls slow staff down, they will be bypassed. This increases risk instead of reducing it. Leaders play a key role in making sure security expectations are realistic.
Accountability also matters. Someone must own each control. Someone must monitor it. Someone must respond when it fails. When ownership is unclear, security gaps grow quietly.
Measuring and Monitoring Over Time
HIPAA Security Standards require ongoing attention. Risk changes as systems, vendors, and workflows change. Monitoring helps organizations stay ahead of problems.
Effective programs include:
- Regular risk reassessments
- Review of incidents and near misses
- Testing incident response plans
Leaders should know how the organization would respond to a security event before one occurs.
Federal guidance reinforces this approach. The U.S. Department of Health and Human Services offers practical resources on ongoing HIPAA Security Rule risk management and incident response preparedness through its official guidance for healthcare organizations.
Organizations that monitor over time are better prepared. They respond faster. They demonstrate diligence. They protect trust.
Preparing for Audits and Enforcement
Audits and enforcement actions often create anxiety for healthcare leaders. That fear usually comes from uncertainty. Leaders are unsure what regulators will ask for or how past decisions will hold up under review.
Preparation changes that dynamic. When HIPAA Security Standards are implemented consistently, audits become manageable events instead of crises.
What Regulators Expect to See
Regulators are not looking for perfection. They are looking for evidence of effort, judgment, and follow-through.
At a minimum, they expect to see:
- Clear and current documentation
- Evidence that risks were identified
- Proof that action was taken to address those risks
Documentation matters, but it must tell a story. Policies should align with operations. Risk analyses should connect to remediation plans. Decisions should be dated, explained, and approved by the right leaders.
A common mistake is assuming documentation alone is enough. Regulators also look for evidence that controls are actually in place and being used.
How Strong HIPAA Security Standards Reduce Audit Stress
Strong HIPAA Security Standards reduce stress because they create consistency. When processes are repeatable and roles are clear, leaders are not scrambling to recreate history during an audit.
Consistency builds confidence. Leaders know what decisions were made and why. Staff understand their responsibilities. Documentation reflects reality.
This also shifts the organization from reactive to proactive. Instead of responding to issues only after they surface, risks are identified and addressed over time. Incident response becomes more organized. Communication improves.
Audits feel less personal and less urgent when security is already part of normal operations. Leaders can focus on explaining their approach rather than defending it.
For more practical guidance on preparing for compliance reviews and building an audit-ready culture, see Audit Readiness in Behavioral Health: How Compliance Officers Lead Beyond the Checklist.
Conclusion
HIPAA Security Standards are not static. Technology changes. Threats evolve. Organizations grow and adapt. Security programs must evolve with them.
Success depends on leadership engagement. Tools and policies matter, but they are not enough on their own. How leaders set priorities, accept risk, and hold teams accountable determines whether security efforts are resilient or fragile.
Security is part of patient care. It protects sensitive information. It supports the continuity of operations. It preserves trust with patients, staff, and communities.
Now is the time to assess where your organization truly stands. Not where policies say you are, but where day-to-day operations reflect reality. If you are ready to take that next step, we encourage you to start a conversation through our Contact Us page and explore how a clearer, more practical approach to HIPAA security can support your organization’s future.
Ready to Talk?
Further Reading
- John Lynch & Associates: Audit Readiness in Behavioral Health: How Compliance Officers Lead Beyond the Checklist
Practical guidance on preparing for compliance reviews, strengthening audit readiness, and building a proactive compliance culture.
- U.S. Department of Health and Human Services: HIPAA Security Rule Guidance
Official federal guidance on risk analysis, safeguards, and ongoing security management expectations. - Health Sector Cybersecurity Coordination Center
Federal threat briefings, alerts, and cybersecurity resources designed specifically for the healthcare sector.
Related Articles

Healthcare Project Risk Management: 7 Red Flags in the First 90 Days

Your Healthcare Project is Live. Now What?